Using Norton™ Personal Firewall
| Getting Started | Working With Firewall Features | Turning Firewall Functions Off and On |
Getting Started
Norton Personal Firewall is your first line of protection against hackers. It automatically locks out intruders and protects your identity and data while you're on the Internet.
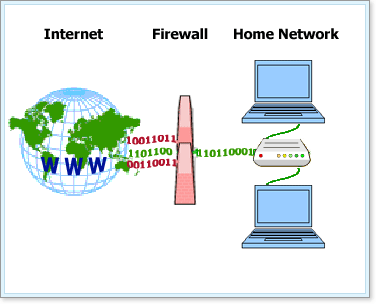
Norton Personal Firewall locks and protects as it monitors the communications between your computer and other computers on the Internet. It protects your computer in the event of common security problems:
| Improper connection attempts | Warns you of connection attempts from other computers and of attempts by programs on your computer to connect to other computers |
| Port scans | Cloaks the inactive ports on your computer and detects port scans |
| Intrusions | Detects and blocks malicious traffic and attempts by outside users to attack your computer |
Use the Online Protection Dashboard to access a Settings list that shows current Norton Personal Firewall status and provides links to settings.
(More Details)
Here's How
-
Launch the Online Protection Dashboard, then click Norton Personal Firewall to open its display.
-
Click the Access Firewall button to access Norton Personal Firewall application details.
-
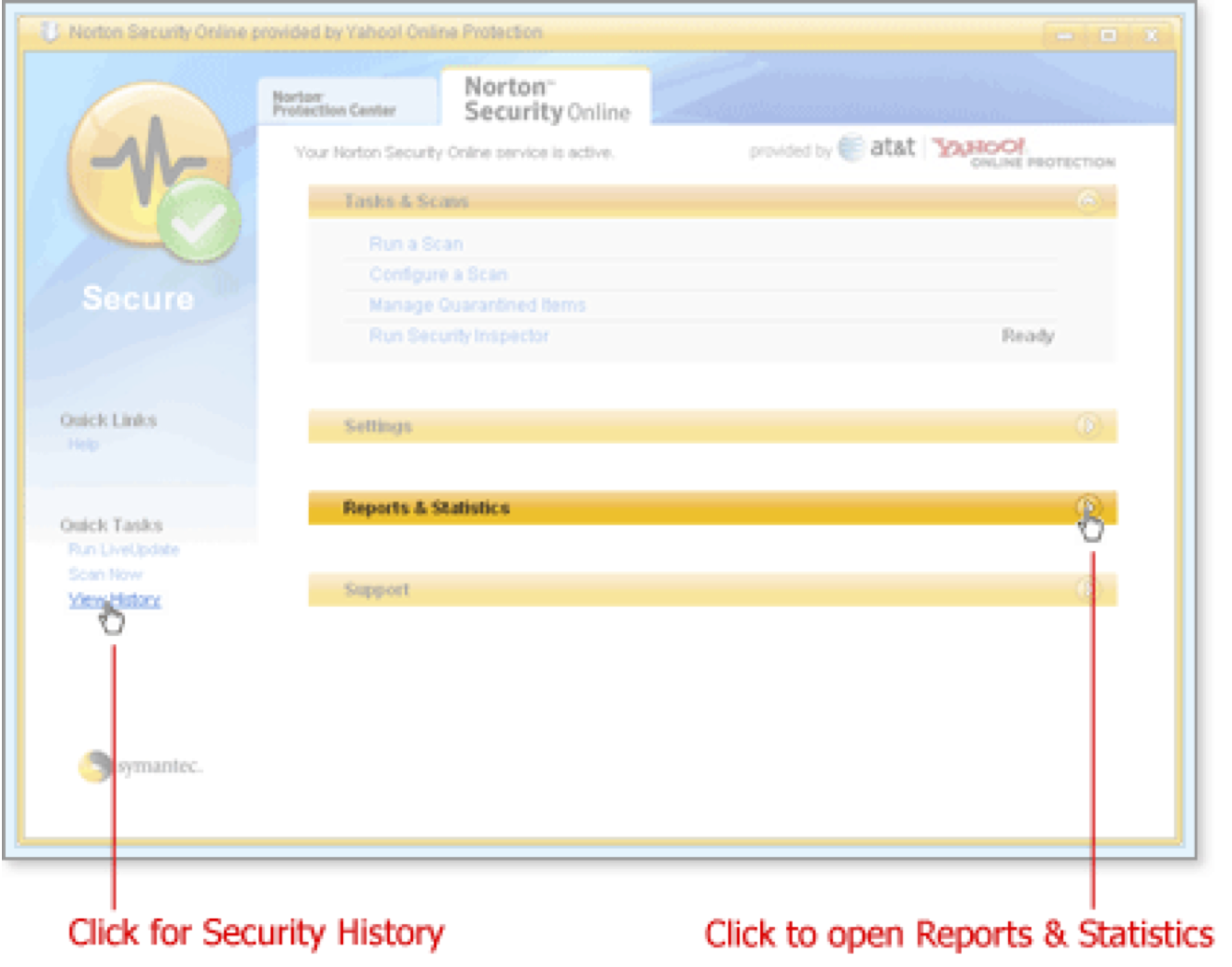
Click View History to examine firewall events. View History provides some interpretation of the events. You can also click the bar named Reports & Statistics, and then View Activity Log for a simple list of events, sorted by category.
-
To open a list of features, click the bar labelled Settings.
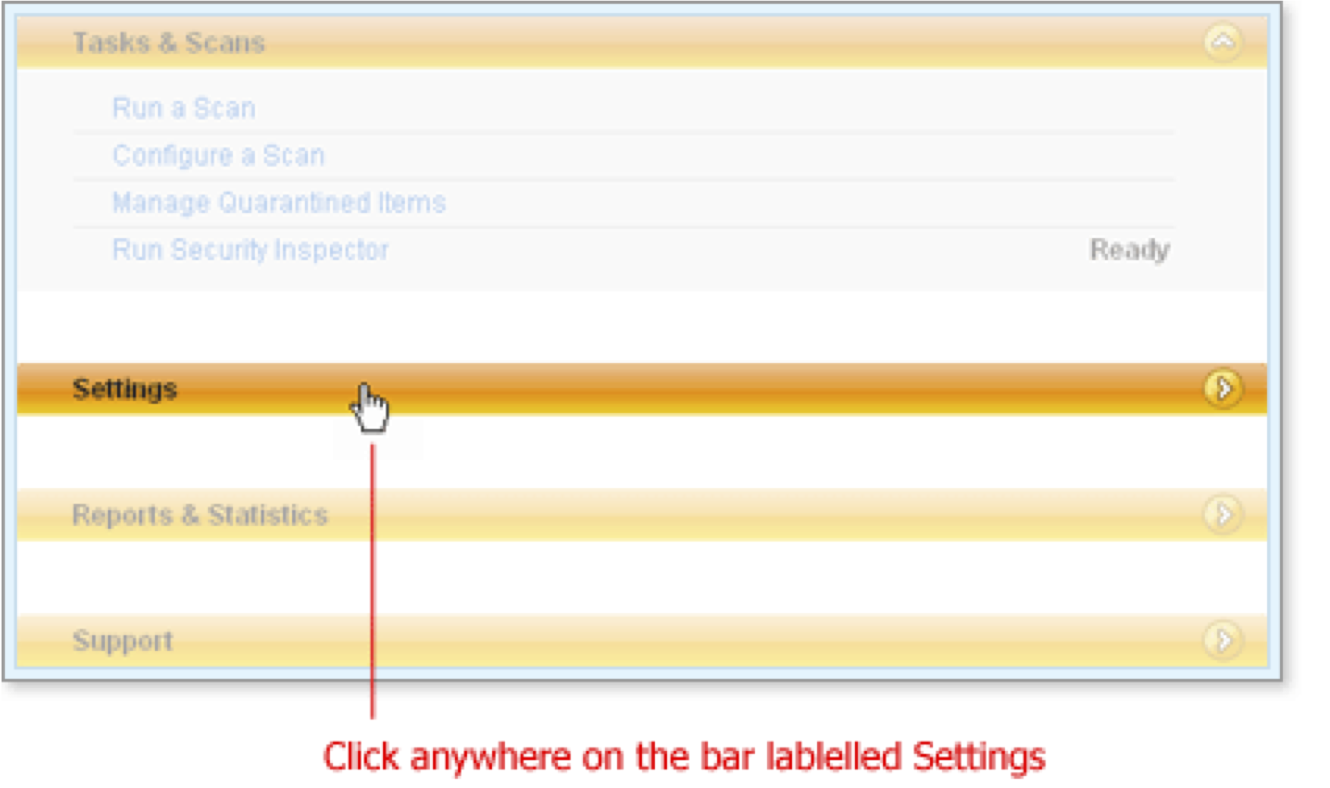
Settings expands to show each feature, its status where applicable, and a link to more feature information and settings.
-
Scroll through the list or expand the window and click Personal Firewall to review or change the settings. You can also click the link Internet Security and Firewall Options for a complete list of settings.
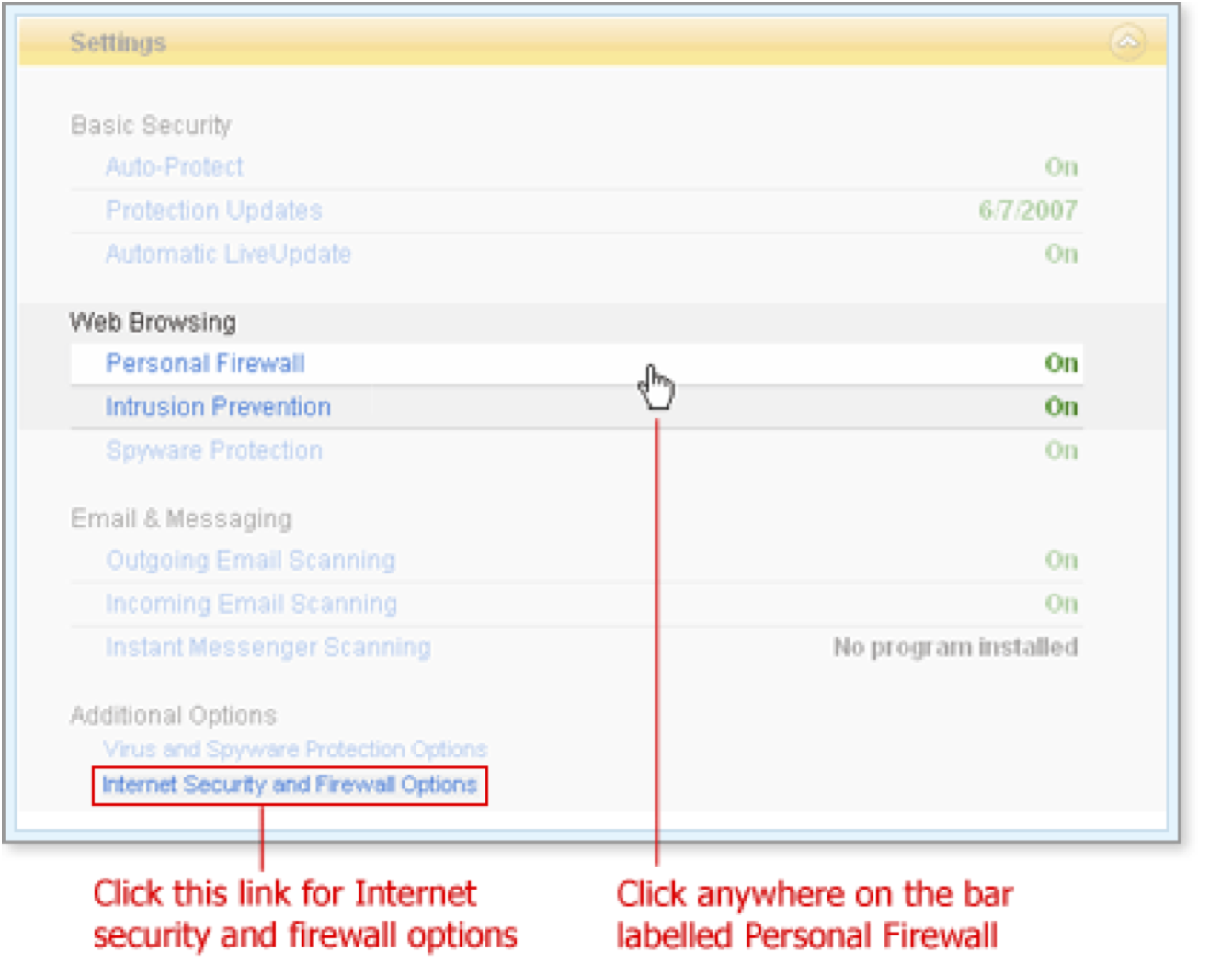
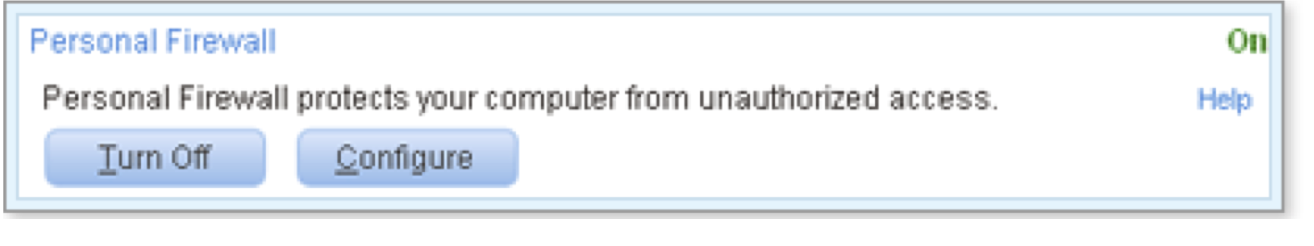
The bar expands to show the buttons Turn Off and Configure and a link for further Help about managing the Personal Firewall.
What's Next
To ensure Norton Personal Firewall meets your protection needs, first configure the features that you want to use.
Words to Know
- ActiveX controls: a set of rules that can be automatically downloaded and executed by a web browser that control how applications should share information.
- Attack signature: a unique arrangement of information that can be used to identify an attacker' s attempt to exploit a known operating system or application vulnerability.
- Hacker: an individual who uses his knowledge of networks and computer systems to gain unauthorized access to computer systems.
- Identity: your AT&T Username or Yahoo! ID. Your identity is closely tied to your Yahoo! profile. You can have more than one identity and choose which one your contacts see.
- Java applet: a program written in the Java programming language that can be included in an HTML page. When you view a page that contains an applet, the applet's code is transferred to your system and executed by the browser.
- Port: a connection between two computers. The connection protocols TCP/IP and UDP use ports to indicate the type of server program that should handle a connection. Each port is identified by a number.