Working With Security History
| Getting Started and Selecting a View | Searching and Examining Details | Quarantining Suspect Software | Restoring Quarantined Software | Submitting a File | Taking Other Actions With Alerts |
Submitting a File
A file identified as a risk might require more investigation for which you don't have time or background. In these cases, you can submit a file for evaluation.
Keep in mind the following points about risks and submitting files:
- In the course of a quick or full system scan, a detected virus or other risk is submitted to Symantec unless you have suspended this feature. In this case, you can submit these items yourself.
- You must have an Internet connection to submit a file.
- Submittal of files to Symantec benefits you in the long run because identified security risks are added to future protection updates.
- No personal data is sent.
(More Details)
Here's How
-
Open Security History and click the current view name. (Remind me how.)
-
Choose Quarantine from near the end of the list that opens.
Security History refreshes with a list of quarantined items.
-
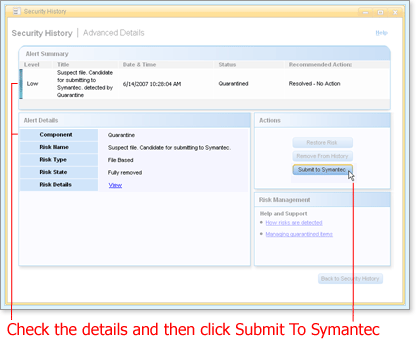
Find the item in the list and open the Advanced Details window by clicking
 in the Title column.
in the Title column.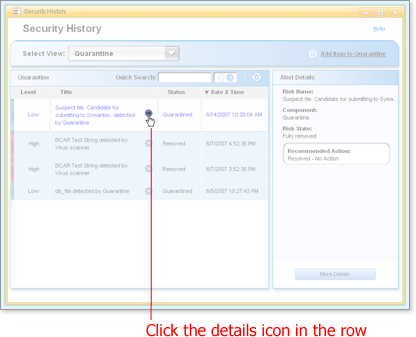
The Advanced Details window opens for the item you chose.
-
Check the details to make sure this risk is the risk you want to submit, and then click Submit To Symantec.
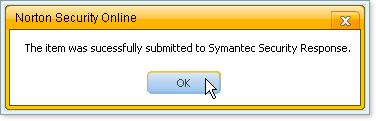
The risk is submitted to Symantec. Successful submittal is reported with a message, and the button Submit to Symantec is replaced by the label Submitted to Symantec.
Note If the risk has already been submitted, Security History assigns a status of Duplicate, and no further action is available for the item. In some cases it is necessary for Symantec Security Response to block submissions of a particular type or size. These items appear as Not Submitted in Security History.
-
Click OK to acknowledge the report.
What's Next
Once a risk is recognized, Norton Security Online generally quarantines it, and the risk is avoided. Removing a risk may become necessary when you want to make the list of risks more manageable.
Words to Know
- Risk: A threat that exploits a vulnerability that may cause harm to one or more assets.